What are NIST Encryption Standards?
Learn about NIST’s encryption standards and why they matter
The National Institute of Standards and Technology is an organization aimed at helping US economic and public welfare issues by providing leadership for the nation’s measurement and standards infrastructure. That’s basically a fancy way of saying they set the standards for things like encryption as it pertains to non-classified government information both in transit and in rest.
Granted, there are a lot of standards, or FIPS, Federal Information Processing Standards, we’re really only concerned with the ones that pertain to encrypted data in motion, or more specifically, as they relate to SSL. Keep in mind, these standards aren’t binding. But they are suggested by the US Government for any and all non-classified data.
So let’s Hash Out the NIST standards for SSL data encryption.
What are NIST Encryption Standards for SSL?
As spelled out in NIST SP 800-175B, Section 3, NIST breaks its cryptographic standards into three categories:
- Cryptographic Hash Functions
- Symmetric Key Algorithms
- Asymmetric Key Algorithms
We’ve written about this before, but here’s a quick refresher:
A cryptographic hash function is really just a cryptographic method for mapping data to a fixed-length output. This provides a useful way for determining the integrity of a piece of data. Now, when we say integrity I’m not referring to someone with a firm moral compass, I just mean that the data hasn’t been altered or tampered with. Here’s an example, let’s saying I’m using SHA-256 to hash a file. When I send the file I’ll send both the file itself, and the unique hash value that was created when I hashed the data with SHA-256. Now, when you receive the data, you can perform the same hash function and if the values match, the integrity of the data is in tact. Keep in mind, even the smallest alteration to the data will result in a completely different hash value.
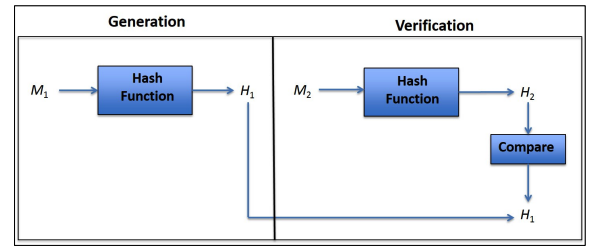
That leaves us with symmetric and asymmetric encryption. Both use algorithms to encrypt data, the difference comes in the decryption. Asymmetric encryption could also be called one-way encryption. The keys are different. You most commonly see this during the SSL handshake, a client will use a public key to decrypt a message that the server will use its private key to decrypt. This is useful during authentication, but for the actual communication you’ll want to use something a bit more agile. That’s where symmetric encryption comes in. Symmetric encryption uses keys that can both encrypt and decrypt – it’s two-way encryption and it’s ideal for communication.
Ok, now that we’ve got a foundation, let’s get into the standards…
What are NIST Encryption Standards for Hash Functions?
FIPS 180 specifies the SHA-1, SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224 and SHA-512/256 hash functions. These are sometimes just known as SHA-1 and SHA-2, the number following the hyphen denotes the length of the output. SHA-1 has been deprecated for the purposes of digital signatures, but may continue to be used for the majority of other hash functions.
Additionally, FIPS 202 outlines the use of SHA-3 at the -224, -256, -384 and -512 output lengths. More guidance on the use of SHA-3 is forthcoming.
What are NIST Encryption Standards for Symmetric Key Algorithms?
Several classes of symmetric algorithms have been approved for use by the NIST, based on either block cipher algorithms or hash-based functions.
Block Cipher Algorithms
- Data Encryption Standard (DES)
- Triple Data Encryption Algorithm (TDEA or Triple DES)
- Advanced Encryption Standard (AES)
Hashed-Based Functions
- HMAC
What are NIST Encryption Standards for Asymmetric Key Algorithms?
Asymmetric algorithms tend to be much bigger and more unwieldy than their symmetric counterparts. There are several asymmetric algorithms approved for use by NIST. They are:
- Digital Signature Algorithm (DSA)
- Elliptic Curve Digital Signature Algorithm (ECDSA)
- RSA
- Diffie-Hellman
- MQV
What are NIST Encryption Standards for Algorithm Strength?
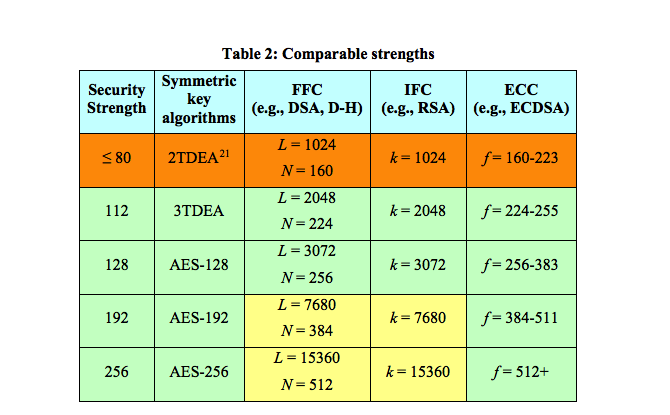
Algorithm strength is crucial element in determining the overall strength of the encryption. Encryption strength is measured in terms of breakability – how difficult would it be for an attacker to break said encryption. The approved security strengths for federal applications are 112, 128, 192 and 256. Previously, 80-bits was allowed but that has since been found to be insecure.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown